AUTOMATE
IDENTITY HYGIENE
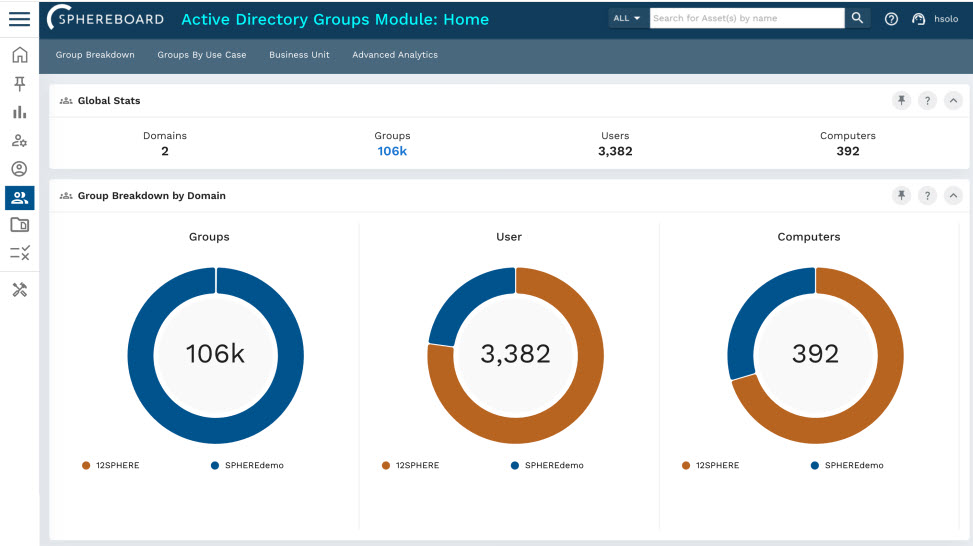
Discover, correct, and prevent your organization’s account, group, and data issues and automate Identity Hygiene from day one with SPHEREboard.

Accelerate
Time-To-Value
SPHERE’s flexible approach lets you zero in on areas that matter most to you:
Get the results you need when you need them.
Because Risk Never Sleeps
By continuously assessing your environment, SPHEREboard enables you to maintain a least-privilege state so gaps get closed and your infrastructure stays clean.
We play well with others
From connecting with source systems to integrating with third-party tools, SPHERE is built to integrate with your existing technology stack. We partner with the industry’s leading identity security, PAM, and data security solutions providers to accelerate implementation and time-to-value.
Your organization has already made significant investments in security, let SPHERE help take it to the next level and automate Identity Hygiene for your organization.
Protect Your Most Critical Assets
84% of organizations experienced an identity-related breach, with an average cost of $4.45M per breach. SPHEREboard helps you take back control of your assets and your budget. See it for yourself.
